Automate Azure Front Door HTTPS
Overview
These are the details of a recent attempt to automate the HTTPS configuration for Azure Front door.
Spoilers: I tried to use ARM, it didn’t work, I had to resort to Azure CLI as a secondary step in the deploy process.
Azure Front Door HTTPS
Providing a secure connection via HTTPS has come along nicely in the past couple years.
Largely thanks to the efforts of companies like Let’s Encrypt, you can now create the certificates needed to secure your communications free of charge.
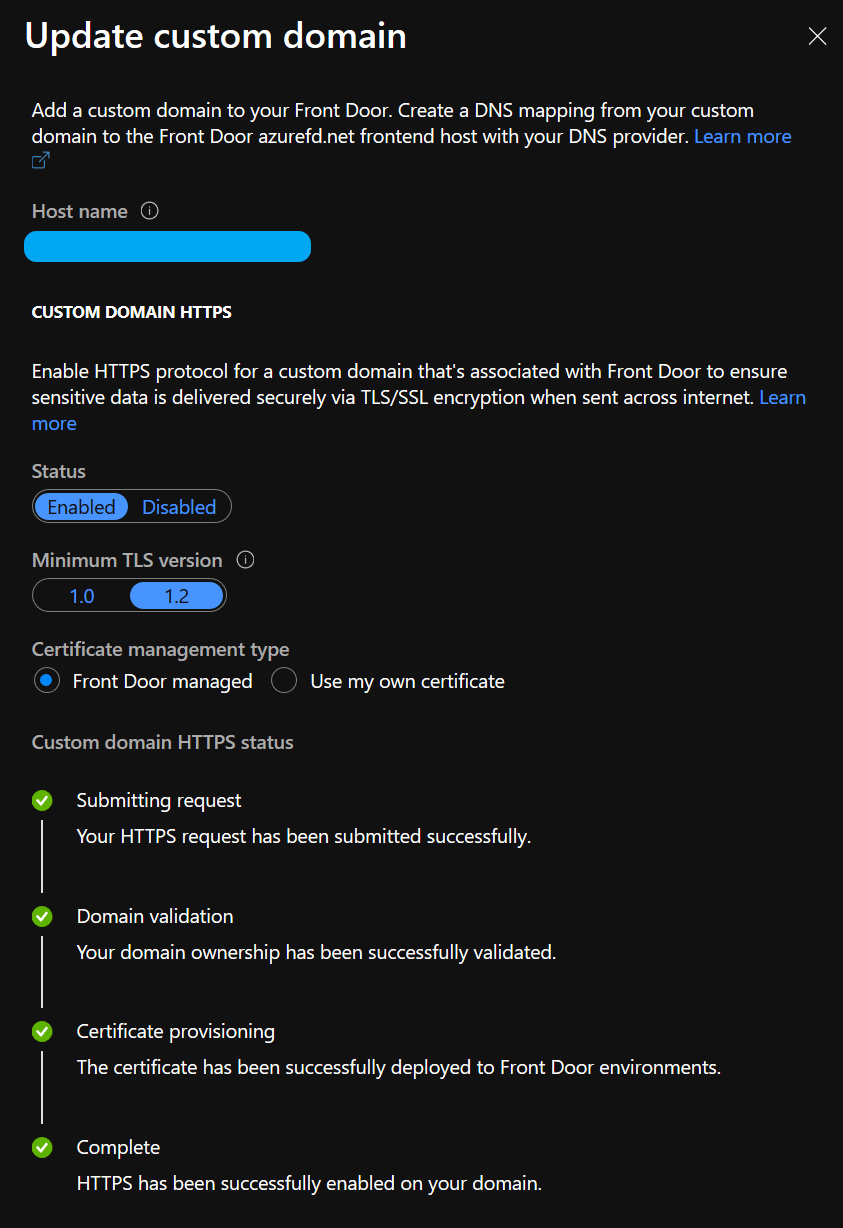
Assuming you have a custom domain associated with your Front Door instance, Azure has two options for enabling HTTPS communications for your custom domain.
- “Front Door managed”
- “Use my own certificate”
The “Front Door managed” version is the variant that I’ll be using for this post.
Front Door managed certificates
By choosing this option, Azure Front door will handle all certificate management tasks for you.
This includes the provisioning of the initial certificate, as well as making sure to renew the certificate whenever appropriate.
No more stress about keeping tabs on certificate expiry and renewal! 🙌
CNAME configuration/domain validation Gotcha
Before diving right into the attempts, lets talk about a gotcha I had along the way.
And by gotcha, I mean, the documentation clearly states it, but I skimmed over it… 🙄
Having previously configured the afdverify CNAME entry to add a custom domain to my front door instance, I had assumed that the same entry would be used to validate the domain prior to provisioning the certificate.
Don’t fall into this trap, it doesn’t work like that, as documented here
Front Door will only automatically validate your domain and provision a certifiate IF the CNAME for the domain is mapped DIRECTLY to your Front Door URI.
For example:
This WILL work: CNAME: www.contoso.com -> contoso.azurefd.net
This will NOT work: CNAME: afdverify.www.contoso.com -> afdverify.contoso.azurefd.net
In my case, there was a CloudFlare proxy in the middle, hiding the azurefd.net origin URI, and preventing the automated validation.
Attempt 1 - ARM (Fail)
After following my usual process for discoverying ARM configuration, I landed on something like this extract from the frontendEndpoints part of the ARM template.
|
|
Unfortunately, while this doesn’t produce any kind of errors when deployed, it also produces no result. I’ve also found the following Stack Overflow question with similar results.
The Solution - Azure CLI
Ultimately my solution is a hybrid ARM + Azure CLI deployment.
I have two tasks in my Azure Devops Release Pipeline
The first task deploys the majority of the Azure resources, the second task configures anything not specifically supported by ARM at this time.
Here is a slightly modified version of the code I’m using for the Azure CLI task.
|
|
Success!